Table of contents
This is the ultimate guide to smart home cybersecurity, this guide was created to help people understand how to secure their smart homes. Security risks running out of control are a major consequence from developing the Internet of Things (IoT) and smart devices. The internet was built to be shared and connected but not secured. Odd that security considerations took a backseat in nearly every aspect of the online architectural design. Many various methods of encryption have been developed in response to disastrous circumstances which had previously occurred. Nothing is foolproof, since we are constantly needing to play a constant game of cat-and-mouse against the cyber criminals.

Unfortunately, the lesson is often learned rather harshly. And the brutal reality is that our safest assumption we can ever make, is to understand something simple. Literally any device connected to the internet can be potentially breached, compromised, or otherwise hacked. IoT manufacturers also tend to pass-the-buck when it comes to protecting their consumers, especially when any security fault or network breach is at play. They don’t want any reason to recall their sold devices nor attract any bad publicity at the same time.
Smart Devices and the Internet
If a device is connected to the internet, then always assume it may have already been breached.
So what can we do about it? Most people are not sure. The reason why is because the answer is difficult, technical, and can be quite complex. If it were easy then everyone would be doing it, pure and simple. That is definitely a big problem which we are seeking to help with through Simius.
Our goal is to help customers keep informed on any weaknesses or vulnerabilities by scanning your network and reporting the results for awareness. We also want to assist with addressing these cyber threats directly and as much as possible, but knowing is half the battle and the first step to taking corrective action remains with the customer.
Cyber Vigilance

Cyber vigilance in the face of an evolving threat landscape is what we as iot consumers need.
If a vulnerability is found, oftentimes the best fix is updated firmware or software. But this is not always the case. Sometimes there is an active threat which might be ongoing without your awareness. When a cyber criminal is able to perform reconnaissance on your network, they can gain information which they can leverage for further exploitation against you.
The Cyber Criminal Goals
Typically cyber criminals will do one of two things once they have compromised your system:
- Quick smash and grab for any loot, or
- Lie low and wait for other opportunities to strike
If your smart home cameras are hacked for example, you may want to consider shutting off the devices immediately, perhaps even by disconnecting your router. Then go about isolating all possible points of failure, from changing default passwords on the router and devices to segmenting them on your network using a VLAN, which separates trusted devices versus untrusted devices into different layers on the network (though some routers might not be compatible with such an implementation). And you don’t necessarily need to be connected to the internet for any of that to be done either. Also, if you have an internet phone that is hard wired to the router, consider also making sure you have good reception and battery charge on your cell phone in case of emergency. (Further reading: Hackers Breach Ring Home Security)

We don’t want to assume that the cyber criminals are watching you from that conspicuous van across the street, but it’s definitely in the realm of possibilities. It cannot be ruled out.
To take yourself out of that vulnerable situation, it is important to not only have a basic understanding of cyber security fundamentals, but also to be aware of how threats can be prevented or eliminated. It’s a big problem that Simius is helping to solve at the first step.
Cyber Reconnaissance
Gain the Advantage over Cyber Criminals
To briefly explain, it is only through testing your cyber security defenses directly, that you can understand where those weak points actually are.
Simius is designed to empower our customers with the same hacking tools used by the criminals, so that we can imitate the cyber attack.
The Lockheed Martin Method
According to lockheed martin, the steps taken by any cyber attack can be summarized as follows
- Reconnaissance
- Weeaponization
- Delivery
- Exploitation
- Installation
- Command & control
- Actions on objectives
We’ll elaborate on all those points later. For now, let us consider the first step of reconnaissance. This is where a network is probed for potential vulnerabilities and backdoors are identified. The next step is weaponizing the vulnerability with some sort of malicious code designed to bypass the security features and acquire further access.
Fortune 500 companies and large enterprises alike, do this all the time. Its standard practice in many industries. They intentionally plan, budget, hire, and execute their own network security tests after carrying out vulnerability assessments. This can include varying levels of penetration testing as well, which seeks to test if a system can be hacked, and if so, it seeks to discover how far the hack can go.
So by imitating the cyber attack and simulating the circumstances using controlled, authorized measures without giving any secrets away, it exposes those unsecured devices which at that point can be further isolated, quarantined, and repaired or replaced if possible.
The Cost of Knowing
Did I mention how expensive all of this is? A single comprehensive penetration test can cost anywhere between $5,000 and $100,000. Vulnerability assessments usually start around a few thousand to over $15,000 and they go up from there as well. Its common to see large corporations schedule either of these quarterly or even monthly. Simius is seeking to offer a holistic solution by hybridizing the vulnerability assessment with penetration testing.
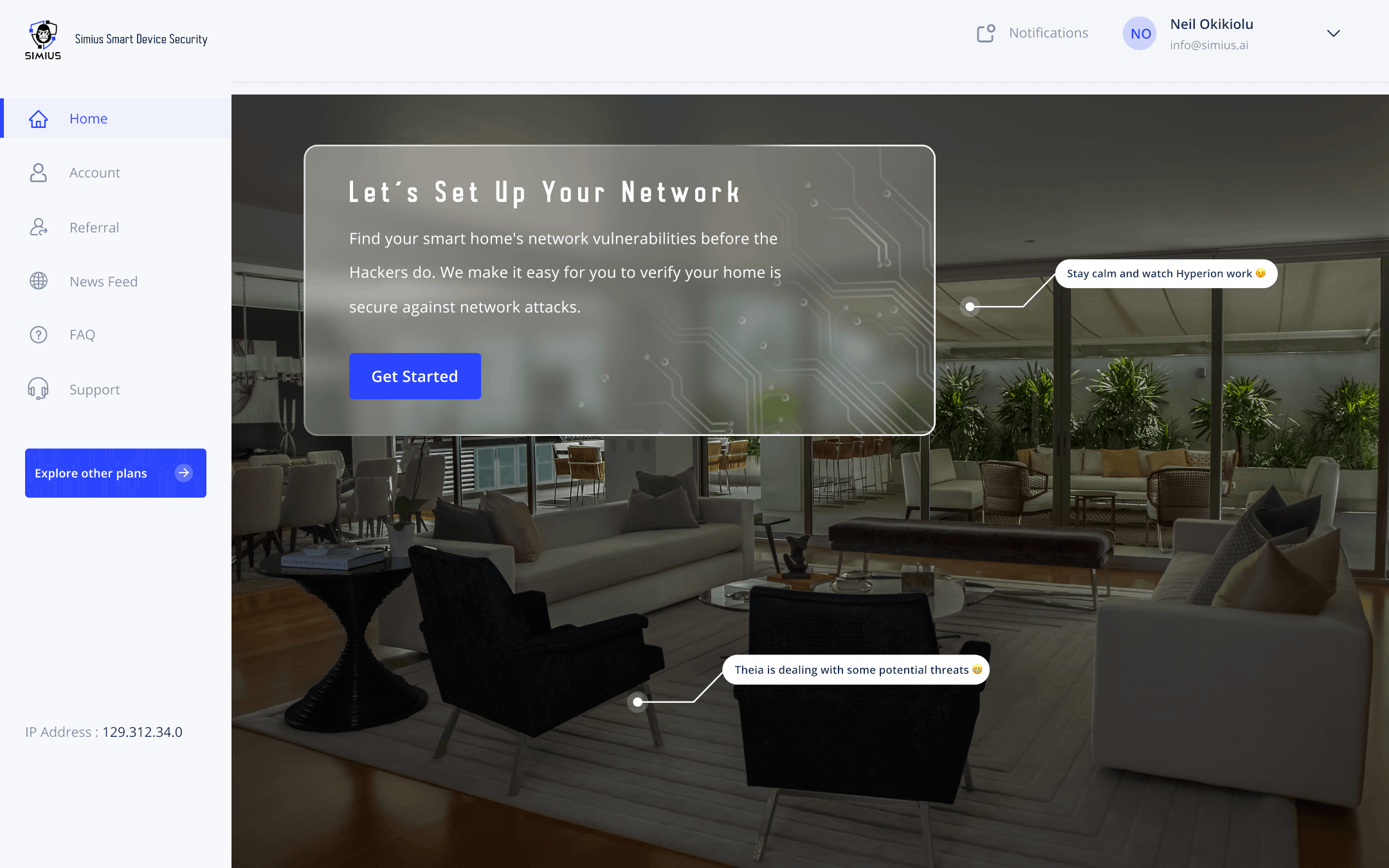
Our Hyperion module is available for scanning and assessing your system for vulnerabilities including open ports, services, credentials, or and basic malware detection, whereas Theia offers a series of network penetration tests against routers and smart IoT devices (such as cameras and other equipment) without actually breaking into your network.
Note that the effects of vulnerability scans and assessments along with penetration tests can also cause systems to crash by exposing bugs or triggering various types of computer crashes. Therefore, we have designed Simius to take a less aggressive approach in targeting surface level vulnerabilities and testing basic modes of exploitation for smart devices.
Again, we don’t expect to crash anything on your network just yet, as these scans do not follow through with any sort of weaponization nor any delivery of malicious code. And while that might come in handy later after building trust to increase the sophistication of what Simius can offer, we still have to start somewhere.
Testing your Cyber Locks
We cyber lock-pick without breaking down the back doors to your smart home network.
Note that the average cost of having a cyber security breach is often greater than the investment into the technology altogether. Whether you had a crypto-wallet stolen, or your home was spied on, an ounce of prevention is worth a pound of cure. Simius will help keep your edge sharp with an easy design that simplifies this complex process of security testing. These network security tests provide you with a level of insight that is easy to understand and designed for you to know how to take action.
What the Test Results Mean
If any device on your network fails our tests, then assume a common cyber criminal could do the same
Hopefully we can beat them to the punch and win at their own game. Think of it like sharpening a blade, except you are using the same cyber weapons that many cyber criminals already have access to. When malware is created, it also gets absorbed into cyber security community which learns how to counter and become effectively immunized against such digital viruses and cyber threats. But this is not always the case. There is no comprehensive standard on patching or mitigation – this is left largely up to the consumer, enterprise, organization, etc.
That said, cyber criminals can still get a hold of these new type of malware and viruses, which they can use against anyone who has not taken the necessary actions to protect their network security. Some vulnerabilities remain with a patch existing, which is why many of the Simius scan results reveal software or firmware updates. Changing passwords, and other recommendations are presented from any issues we detect.
With the advent of IoT devices, smart home owners have largely been left to bite the dust. As these security testing tools are often only used by teams of cyber professionals who are specialized in their field and are trained or experienced in how to use the technical software. Apart from the IoT manufacturers leaving consumers out to dry when things go bad, there is little else that can be done other than to take matters into your own hands.
The Price of Your Data

Data is the number one asset for any organization. the same is true for individuals and families.
Simius is offering security testing out of the gate for a very low, affordable price, and at a tiny fraction of the cost that large corporations pay. Consider paying $10,000 per month versus $10.00 and for the same level of cyber security testing. The value is intrinsic and sophisticated.
By fulfilling the first stage of a cyber attack, smart home owners can correct problems directly at the source. This obviously prevents further downstream harm and reduces risk.
We want nothing more than to help you remain as safe as possible, by offering enterprise-grade cyber security tools in a manner that is simple, effective, and easy to use.
Summary
In this ultimate guide, we discussed the reasons hackers breach your network and the methods they use to hack your network.
In addition, we discussed how enterprises defend themselves and how these defense methods can apply to you as well.